Computer Security Category
Trojans Perform Malicious Functions During SystemDefender Installation
Tests conducted by our threat research team on several computer testbeds have revealed that during the installation process of SystemDefender a Trojan infection starts to perform malicious activities that include the execution of hidden files. SystemDefender is known as a rogue anti-spyware program that when installed it displays popups or messages stating that you have an infection.
Upon further investigation, we’ve detected that it wasn’t just one Trojan but many trojans that are known to be variations of Trojan.Downloader and Trojan Vundo. The Trojans perform several bad actions such as displaying a “Warning” message on your desktop background and not allowing you to open certain programs. These types of Trojan infections can be very detrimental to the operation of your computer.
The following symptoms take place after installing SystemDefender:
- “VIRUS ALERT!” appears in the system tray (lower right hand corner of your desktop)

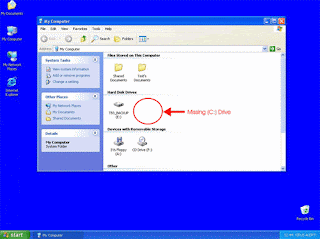
2. The Trojan infections will hide the C: drive icon in the My Computer window.
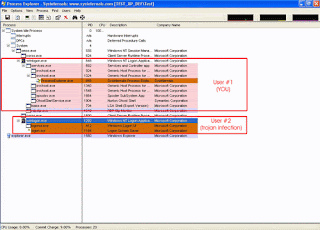
3. The Trojan infections create a new hidden User which is used to execute malicious actions without your knowledge.
5. You’re not able to open any programs.
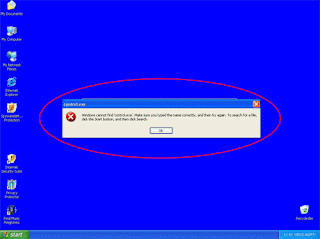
So how do I open SpyHunter if I can’t open any programs?
That’s a good question! The reason that you’re not able to open any programs, including SpyHunter, is because the Trojan infections have created another hidden User profile in your computer which overwrites whatever function that you try to perform as the current User. If you want to open SpyHunter, you can follow the steps below:
Note: These steps only apply to computers that have SpyHunter already installed. If you currently do not have SpyHunter, it is highly recommended you try SpyHunter’s Spyware Scanner for FREE.
- Right-click the SpyHunter icon.
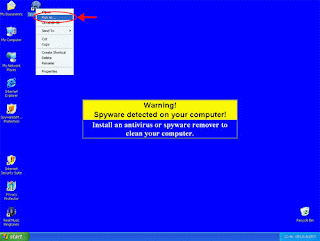
3. Choose the User that is currently logged on (in other words, your User account name), add password, and click the “OK” button.
4. SpyHunter will open and you’ll be able to run a scan.
By applying this method, you’ll be able to overwrite the Trojans’ ability to stop a program from opening.






0 comments: to “ Computer Security Category ”
Posting Komentar